How can I access my servelet inside my VPC after it's provisioned?
Your servelet within the VPC is on a private network, using private IP addresses. There is a virtual router (VR) in front of your servelet, which perform routing with NAT (network address translation), as well as providing inbound (ingress) and outbound (egress) firewall, port forwarding, load balancing and VPN (virtual private network).
Two compulsory steps you need to do before you can access your servelet are:
- Set the outbound (egress) firewall rule to allow all traffic. By default, it's disabled.
- Set the inbound (ingress) firewall rule and port forwarding to allow incoming traffic to your servelet, including SSH (for Unix) or RDP (for Windows) ports so that you can access your servelet remotely.
Setting Up Outbound (Egress) Firewall Rule
For your servelet to be able to access the Internet through the VR gateway, you need to setup the outbound (egress) firewall rule on your VPC to allow all outgoing traffic. By default, all outgoing traffic is denied. You only need to do this once after your VPC is setup or after your first servelet is setup. You don't have to re-do this again for your subsequent servelet setup.
Login to the portal, go to your VPC's control panel: Services > Virtual Private Cloud and click on your VPC plan. Select the "Network" tab, and then click on "Outbound Firewall" as shown on below screenshot.
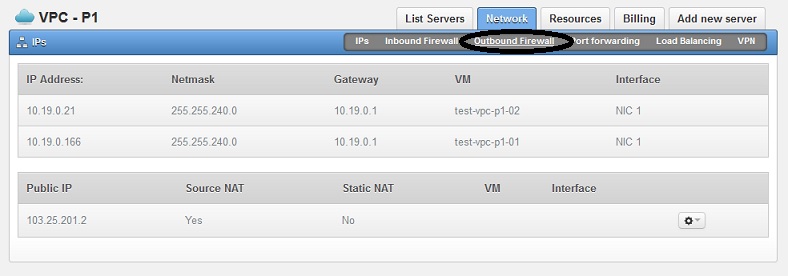
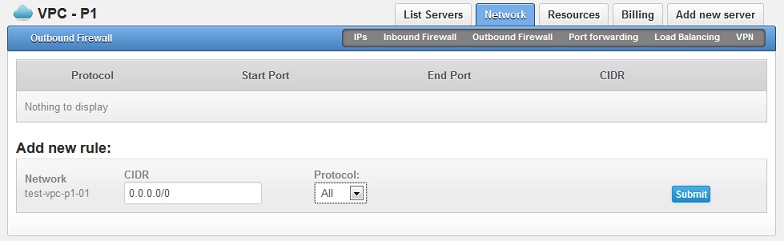
Add a new outbound firewall rule:
CIDR: 0.0.0.0/0
Protocol: All
See below screenshot:
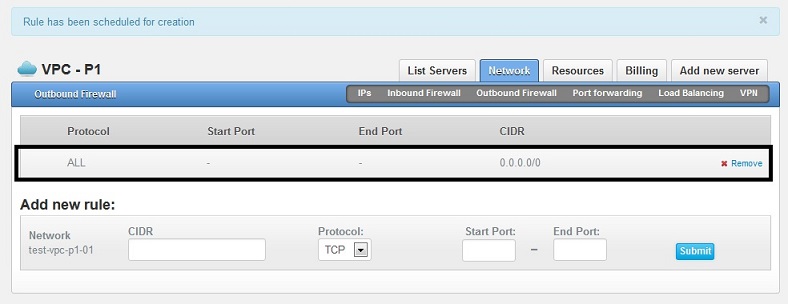
You will see a message stating that the rule has been scheduled for creation and that the new rule will be listed, see below screenshot:
Setting Up Inbound (Ingress) Firewall Rule and Port Forwarding
For you to access your servelet remotely, you would need to set up inbound (ingress) firewall rule and port forwarding for the ports you are going to use (e.g. port 22 for SSH on Unix servelet, or port 3389 for RDP on Windows servelet). Setting up inbound firewall rule and port forwarding is also required for your servelets to accept incoming connections for its services, such as port 80 for web services, port 25, 110 and 143 for mail services, etc.
To setup the inbound firewall rule and port forwarding, login to the portal and go to your VPC's control panel: Services > Virtual Private Cloud and click on your VPC plan. Select the "Network" tab, and then click on "Inbound Firewall". See sreenshot below.
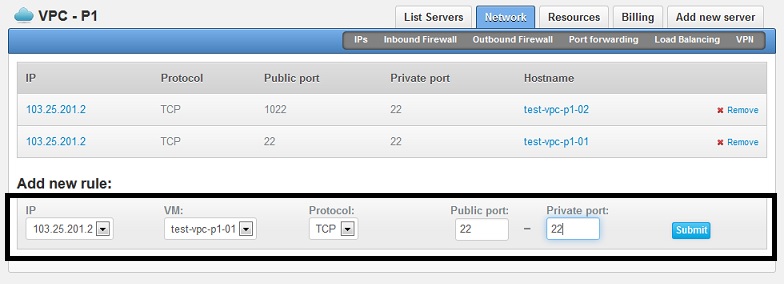
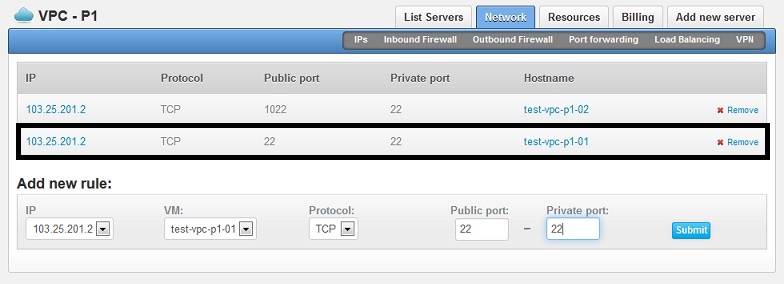
In this example, to map your VPC's public IP address on port 22 to your servelet's private IP address, also on port 22, under "Add New Rule":
- Under IP, select the public IP address of your VPC (in this example: 103.25.201.2)
- Under VM, select the servelet that you want to map to (in this example: test-vpc-p1-01)
- Under Protocol, select the protocol of the port that you want to map (in most cases, it's TCP)
- Under Public Port, key in the port number of the public IP you want to map from (in this example: 22)
- Under Private Port, key in the port number of your servelet's private IP you want to map to (in this example: 22)
Click "Submit". Once the rule has been added, it will be on the list of port forwarding rules of your VPC. See screenshot below.
You can do the same for other services that you would like to run on your servelet, such as port 3389 for Remote Desktop Connection (if you are running Windows servelet), port 80 for web services, port 25 for SMTP services, port 110 for POP services, port 143 for IMAP services, port 21 for FTP, etc.
You can also have a port number on your servelet (private side) to be mapped to a different port number on the public side. On the above example, the SSH port 22 of test-vpc-p1-02 servelet is being mapped to port 1022 on the public side, so we need to use port 1022 if we want to SSH into test-vpc-p1-02 servelet. This is also useful if you only have one public IP address but you have multiple servelets behind and need to have common access (e.g. SSH) to all the 3 servelets. By using different ports, you can share the same IP address for the purpose.
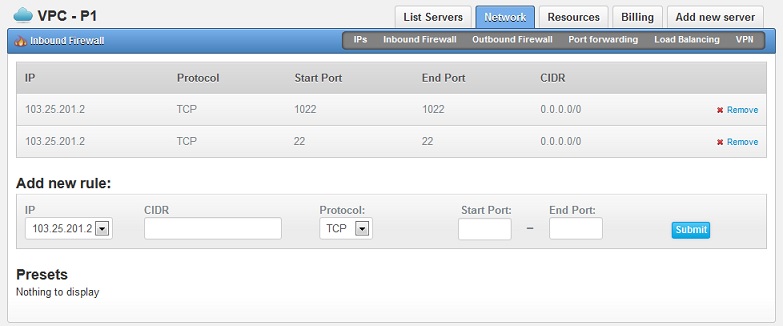
When a port forwarding rule is being created, the correspondence inbound firewall rule will also be created automatically. In the above example, port 22 and 1022 are being used so inbound firewall rules for the two ports will automatically be created. You can check by going to the "Inbound Firewall" tab on your VPC control panel, as per below screenshot.
If you are not familiar with inbound/outbound firewall rules and port forwarding, you can engage our Managed Firewall Service at just $30/month, and we will configure all the rules for your VPC.
☹Dislike0 ☺Like0
 ??
?? English
English Bahasa Indonesia
Bahasa Indonesia ???
??? Espanol
Espanol